Asuri_2019 赛队的 wp 。辛苦各位 Asuri 战队队员了。
Web
JustSoso
Index.php
1 | <html> |
Hint.php
1 |
|
从SugarCRM v6.5.23 PHP反序列化对象注入漏洞分析了解到可以把以下 payload
1 | O:6:"Handle":1: |
中的 1 改成比 1 大的数可以在反序列化时绕过__warkeup魔术方法
绕过$this->token === $this->token_flag的判断可以直接通过爆破来绕过
贴一下脚本:
1 | import requests |
love_math
1 |
|
一上午都在懵逼,要么找到可以突破的数学函数,要么突破正则,应该就是这两种思路了。数学函数都看了一遍,貌似没有什么可以利用的函数。正则匹配/[a-zA-Z_\x7f-\xff][a-zA-Z_0-9\x7f-\xff]*/,这个是 php 变量文档中匹配有效变量名的正则。感觉两个思路都不对…最有可能的还是突破数学函数…数组可以绕之前的,但是eval不能执行
看了好几遍直到看到了base_convert可以在进制转换上做文章,而且根据php文档–base_convert,我们可以知道
1 | frombase 和 tobase 都只能在 2 和 36 之间(包括 2 和 36)。高于十进制的数字用字母 a-z 表示,例如 a 表示 10,b 表示 11 以及 z 表示 35。 |
也就是第二位,第三位参数可以在 2 到 36 之间,而且高于十进制的用字母表示!既然拼接进去的都是字符串,转换出来拼接进去应该可以执行。

本地使用base_convert(55490343972,10,36)()成功执行phpinfo,远程也执行了phpinfo看看是不是有什么问题,看了一圈然而并没有发现什么问题。
然后尝试使用各种执行命令
1 | base_convert(15941,10,36); //cat |
虽然可以执行ls了,看到了flag.php,但是读不到就比较难受了。然后直接就考虑到了是不是可以有cat *这种操作,但是空格跟*都无法编码…这就比较头疼了。而且主要是还得全为数字,有字母的的话就会进whitelist的判断了。
所以可能要尽量避免去使用十六进制什么的含有字母的,考虑到 ascii 码可以转换,又尝试了使用chr函数去转换
1 | ($pi=base_convert(9453,12,36)).$pi(101).$pi(120).$pi(101).$pi(99)($pi(99).$pi(97).$pi(116).$pi(32).$pi(42)) |
一般的构造结果肯定不行…所以这里想用`ls`这种形式去执行命令,但是由于拼接的原因,一直不能执行…思路卡了很久。
看了一些相关十六进制处理的函数,直到看到了两个函数,一个hex2bin函数,是可以把 16 进制转换成字符串,一个dechex函数,把十进制转换成十六进制。
于是我们可以有
1 | php > echo base_convert('636174202a',16,10); |
这样我们就可以把*这个十六进制为2a的转成十进制纯数字的了。
但是我们要怎么利用hex2bin呢,想到可以利用base_convert赋值变量的方式,找到最短的字符串pi,利用$pi=base_convert(37907361743,10,36)构造出hex2bin。
而且还因为echo可以接受如下的拼接方式,例如
1 | php > echo (1).`id`; |
尽量取最短的,这里肯定我们就用,这个形式。
所以大致思路就差不多出来了利用base_convert构造hex2bin,然后用最短的可以执行命令的exec函数去执行cat *的命令
1 | $pi=base_convert(37907361743,10,36),$pi(65786563)($pi(dechex(426836762666))) |
然而没成功…不知道哪里错了,感觉没道理…
1 | ($pi=base_convert),$pi(696468,10,36)($pi(37907361743,10,36)(7267726570206167)); |
接着队友说可以用rgrep ag去弄,而且本地打通了…但是远程以上没打通…我又修改了尝试去rgrep fl,也没打通,当时是这样的

写 wp 的时候,突然又发现可以打通了…

也是神奇…最后当时还是按照自己的思路去走了,感觉是不是哪里出问题了,确定有flag.php,最后尝试修改cat f*,
1 | php > echo base_convert('63617420662a',16,10); |
1 | $pi=base_convert(37907361743,10,36),$pi(65786563)($pi(dechex(109270211257898))) |
拿到 flag(复现环境下)

Pwn
your_pwn
可重复利用的单字节读写的漏洞.

先直接读取栈上的返回地址泄露pie基址.
然后构造ROP链打印库函数地址泄露libc.直接调用system(binsh);获得flag.
1 | from pwn import * |
daily
remove的时候没有对index进行范围检测.

先利用unsorted bin泄露libc,再利用fastbin单链表泄露heap基址.
申请一个chunk,在里面伪造一个堆指针和对应的faker chunk.free掉这个faker chunk,通过edit构造其fd到bss上,由于length可控,通过remove构造出一个chunk头部绕过检查.
成功fastbin attack,获得任意读写的能力,由于程序开了Full RELRO所以劫持__free_hook调用system(binsh);获得flag.
1 | from pwn import * |
baby_pwn
ret2dl in x86,没有可供leak的函数.保护很少,想起之前的0ctf2018 babystack,修改脚本直接打,成功.
1 | import sys |
Virtual
感觉难度主要在于逆向,理解程序逻辑.

首先是store_instruction函数将输入通过分隔符分类为各种操作符并保存在堆中,store_num同理.
其中三个堆块一个数据堆,一个操作符堆,一个栈(也是用来存数据的,存储操作符操作的数据).
重点就是op函数.

这里不断从操作符堆取出操作符(对应的数字),然后跳转到函数执行的地方,这里IDA反汇编有问题,没有识别出函数调用,实际上i会被赋值为函数调用的返回值.
这些函数操作栈中的数据并将结果放回栈中,所以使用数据前需要先push.
关键函数是load和save,知道偏移就可以任意读写.
先使用load泄露堆上的堆地址,由于没开pie,通过-和/求出.got[puts]和此处偏移,再次load泄露libc,处理与system的偏移获得system地址.
不过这里没办法复制保存数据,只能移动和计算,所以之前的偏移没了,通过同样操作调整一下再次获得.got[puts]偏移,调用save成功劫持puts@plt.
突然发现username作用,开始试了/bin/sh,ls,cat flag什么的都是comment not found,最后/bin/bash成功.(话说这是故意的还是什么鬼)
payload
1 | from pwn import * |
Double
新增node时 ,会出现重用指针的情况, 导致后面的 uaf
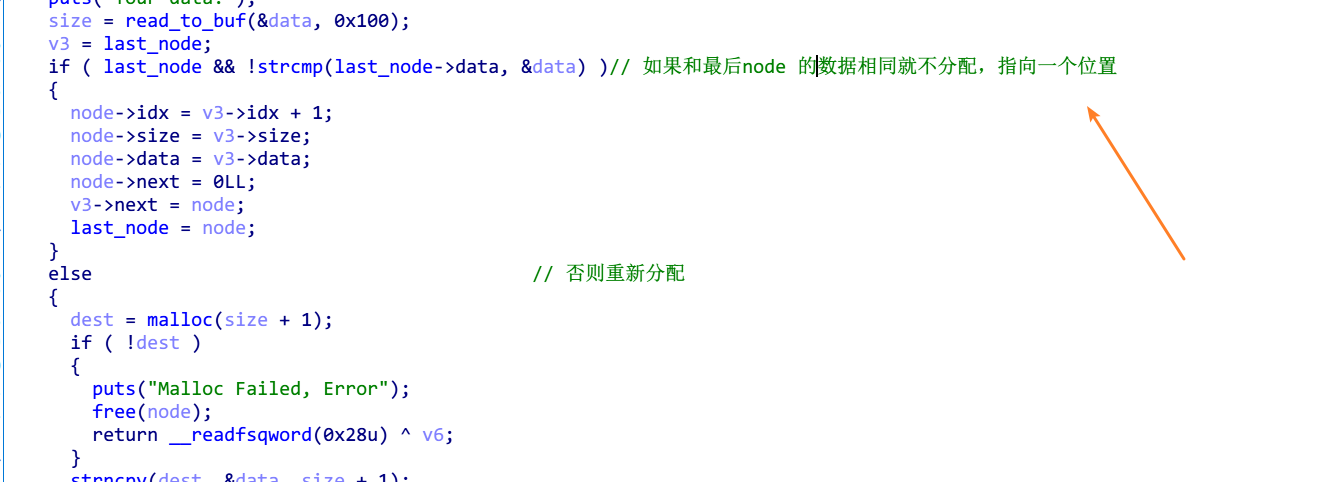
然后 fastbin 改 malloc_hook
1 | #!/usr/bin/python |
Misc
签到
三人出境即可
saleae
通过提示找到 saleae 这个软件,将数据导入,选择 SPI 协议进行分析,可以得到 flag。
导出的分析报告如下:
1 | Time [s],Packet ID,MOSI,MISO |
即
1 | flag{12071397-19d1-48e6-be8c-784b89a95e07} |
24c
和上一道题类似,导出的数据报告如下:
1 | Time [s], Analyzer Name, Decoded Protocol Result |
这个神奇的地方在于在接收完后又进行了修改,但是修改哪个地方是很大的问题。制表符一般会跳过 8 个字节,我其实也没想通为什么是这样,不过我尝试了 n 多次,最后终于试出来改变的位置了。
1 | flag{c46dac10-e9b5-4d90-a883-41cf163bdf4e} |
usbasp
用之前提供的软件,将协议切换为 SPI,其中的设置修改这里:
1 | Enable line is active high |
可以得到如下输出:
1 | Time [s],Packet ID,MOSI,MISO |
就可以得到 flag 了。
Rev
easyGo
用 IDAGolangHelper 以 Go1.10 版本恢复符号后,动态调试。
在 base64 解码之后下断点,大概位置在:
1 | .text:00000000004952EB call encoding_base64__ptr_Encoding_DecodeString ; encoding_base64__ptr_Encoding_DecodeString |
处。此时查看 rdx 寄存器会发现里面保存着 flag。

1 | flag{92094daf-33c9-431e-a85a-8bfbd5df98ad} |
Crypto
puzzles
question 0 解多元方程
a1=4006,a2=3053,a3=2503,a4=2560 0xfa6 bed 9c7 a00
question 1
前1个和后面2个分别是质数序列上的等差数列,推测出part1
part1=26365399 0x1924dd7
后面3个就是大物高数问题,直接求解答案
question 2
part2=(1+6^3-5^3+7+1)*77=7700 0x1e14
question 3
part3=18640 0x48d0
question 4
part4=120*336=40320 0x9d80
最后合并起来获得flag
warmup
阅读源码会发现,输入空可以得到 flag 的加密值,我们可以因此爆破 flag。
爆破脚本:
1 | from pwn import * |